Using Google bq CLI, the following command allows to get the top Pypi keywords from the bigquery-public-data.pypi.distribution_metadata table:
bq query --use_legacy_sql=false 'SELECT keyword, COUNT(*) as keyword_count FROM `bigquery-public-data.pypi.distribution_metadata`, UNNEST(SPLIT(keywords, ", ")) as keyword GROUP BY keyword ORDER BY keyword_count DESC LIMIT 100'Result for the top-15 keywords:
python: 128555 appearancesDuckDB Database SQL OLAP: 70739 appearancesai: 64997 appearancestensorflow tensor machine learning: 51144 appearancespulumi: 50076 appearancesapi: 47986 appearancesprobabilities probabilistic-graphical-models inference diagnosis: 46552 appearancesrust: 45607 appearancescli: 39512 appearancesOpenAPI: 38814 appearancessdk: 38060 appearancesllm: 37487 appearancesOpenAPI-Generator: 36734 appearancesdatabase: 35578 appearancesautomation: 34393 appearances
Note that this is a very basic query, that does take into account that some packages have a lot more versions published on Pypi than others.

Project documentation: pdfly.readthedocs.io
pdfly is the youngest project of the py-pdf organization.
It has been created by Martin Thoma in 2022.
It's simply a CLI tool to manipulate PDF files, written in Python and based on the fpdf2 & pypdf libraries.
I'm a maintainer of the project 🙂
What can it do & what's next?
Find out by reading the full article
Outil permettant la mise à l'échelle de n'importe quelle image de style "anime", par le biais de réseaux de neurones convolutionnels. Fonctionne également sur les photos.
Open-source: https://github.com/nagadomi/nunif
Added
- support for Output Intents on document level - thanks to @lka
- support for shading patterns (gradients) - thanks to @andersonhc - PR 1334
- support for setting a minimal row height in tables
- support for
v_alignat the row level in tables - new optional
reset_page_indicesparameter forinsert_toc_placeholder() - support for
strikethrough text - support for
first_line_indentintext_region.Paragraph - new ViewerPreferences.print_scaling
- documentation on
fpdf2internals - documentation on generating Aztec Codes
- added Slovenian translation of the tutorial: Vodič - thanks to @DeepBlackHole
- support for adding TrueType fonts that are missing the
.notdefglyph - issue 1161 - thanks to @spacegaori - improved SVG image parsing speed by 50% to 70% - thanks to @petri-lipponen-movesense - PR 1350
- added tutorial "tuto7" (in English and German) with documentation to create PDF/A files with fpdf2 - thanks to @lka
Fixed
FPDF.write_html(): Fixed rendering of content following<a>tags; now correctly resets emphasis style post</a>tag: hyperlink styling contained within the tag authority. - issue 1311- FPDF.footer() does not "leak" its text style to the table of contents anymore
FPDF.table(): Fixed heading styles containing underline failing to render.FPDF.ln(): the method now allows a value of0to be provided forh.- font optimization: only include fonts effectively used in the final PDF document. Fonts added via
set_font()oradd_page()but not actually used in the document are no longer included in the final output. This reduces file size and improves performance, especially for documents with many fallback fonts. - issue 1382 - a
KeyErrorwas raised in some specific cases when auto-downscaling images - issue 1409Changed
- heading rows of tables are never rendered "alone" on a page anymore
... and how to use them in CI pipelines.
Comparing W3C v.Nu HTML checke, html-tidy, htmlhint, html-validate, LintHTML and html-eslint.
Au cours des 18 derniers mois, j'ai eu l'occasion de concevoir plusieurs sites web pour des proches et des associations où je suis bénévole.
Dans cet article, je reviens sur mes choix de solutions pour les mettre en place, et partage mes réflexions concernant les alternatives pour concevoir de "petits …
A short Python script based on pypdf that checks if PDF files contain JavaScript code, and if applicable print it.
Pwning Python 3 VM via an intended feature (Disclaimer: Not a vulnerability)
Sections:
- Indexing into Known Memory
- Creating a call gadget
- Changing the page permissions using ctypes
- Crafting our Shellcode
I wrote my last post on fpdf2 18 months ago.
We released 7 more versions of fpdf2 since then!
This article will present some of the major features introduced since v2.7.3 to v2.8.1 of fpdf2:
click on the buttons below to reveal the various changes brought …
Latest informations on Pypi and related security / vulnerabilities...
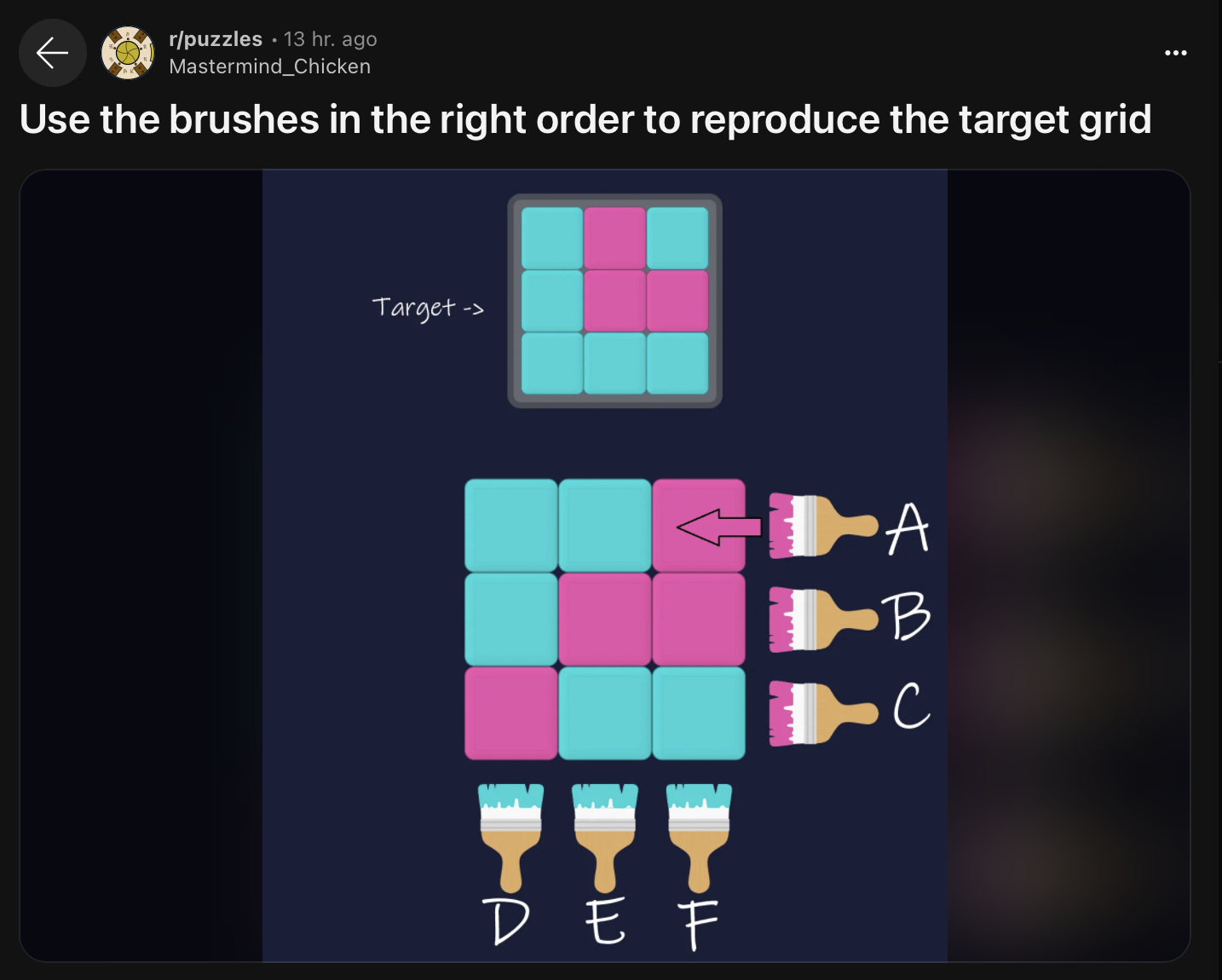
I discovered this coding puzzle in numero 4 of Paged Out, on page 32.
I found it fun and wrote my own solution in Python: paintbrush.py
It reminded me of Project Euler problems.
I recommend to give it a go based on the Paged Out one-page article, without reading Alperen Keles answer or mine! 🙂
RMBG v1.4 is our state-of-the-art background removal model, designed to effectively separate foreground from background in a range of categories and image types. This model has been trained on a carefully selected dataset, which includes: general stock images, e-commerce, gaming, and advertising content, making it suitable for commercial use cases powering enterprise content creation at scale. The accuracy, efficiency, and versatility currently rival leading source-available models. It is ideal where content safety, legally licensed datasets, and bias mitigation are paramount.
FROM: Underscore_ @ YouTube
There already are multiple blogging solutions which are part of the Fediverse.
ActivityPub, the network protocol behind the Fediverse can only be fully implemented by means of an active server component: Among other things, incoming messages delivered to inboxes have to be processed. Sometimes they need to be forwarded, and outgoing messages need to be signed.
Nevertheless I wanted to figure out, which parts of the ActivityPub protocol can be implemented in a purely static website, and how well other servers in the Fediverse interact with it. My goal was to attach this blog to the Fediverse. The blog is generated using the static site generator software Pelican.
We live in a world that is gradually and incessantly attracted by over-rationality and order. In this article we’ll burst the enchanted bubble and embrace corruption and chaos — We’re going to discuss the topic of image glitch art.
tomato is a python script to glitch AVI files
It was designed to operate video frame ordering, substraction and duplication.
Youtube generates revenue from user ad views, and it’s logical for the platform to implement restrictions to prevent people from downloading videos or even watching them on an unofficial client like YouTube Vanced. In this article, I will explain the technical details of these security mechanisms and how it’s possible to bypass them.
...
Since mid-2021, YouTube has included the query parameter
nin the majority of file URLs. This parameter needs to be transformed using a JavaScript algorithm located in the filebase.js, which is distributed with the web page. YouTube utilizes this parameter as a challenge to verify that the download originates from an “official” client. If the challenge is not resolved andnis not transformed correctly, YouTube will silently apply throttling to the video download.The JavaScript algorithm is obfuscated and changes frequently, so it’s not practical to attempt reverse engineering to understand it. The solution is simply to download the JavaScript file, extract the algorithm code, and execute it by passing the
nparameter to it.
...
Many projects currently use these techniques to circumvent the limitations put in place by YouTube in order to prevent video downloads. The most popular one is yt-dlp (a fork of youtube-dl) programmed in Python, but it includes its own custom JavaScript interpreter to transform the n parameter.
No More GIL! the Python team has officially accepted the proposal (PEP-703)
Aujourd’hui on se penche sur une technique de piratage très maligne, vu qu’elle repose principalement sur : votre répondeur. Martin Vigo, un expert en cybersécurité, a mis au point un soft qui permet d’exploiter des répondeurs du monde entier. En y accédant, il peut ainsi aller réinitialiser les accès de nombreux services utilisant la double authentification, comme Whatsapp, Paypal, Facebook ou encore Linkedin, bref, tous les services qui peuvent vous envoyer un code par téléphone.

Pylint is a great static code analyser for Python code. I have been using it for several years, in various projects, and it's simple to use yet very powerful.
I even contributed to Pylint by submitting a new rule a few years ago : implicit-str-concat.
For an introduction to Pylint, you …
open-source non-profit search engine for shadow libraries, like Sci-Hub, Library Genesis, and Z-Library
🔍 Moteur de recherche des bibliothèques clandestines : livres, journaux, BD, magazines. ⭐️ Bibliothèque Z-Library, Bibliothèque Genesis, Sci-Hub. ⚙️ Entièrement résilient grâce à un code et à des données open source. ❤️ Faites passer le mot : tout le monde est le bienvenu ici !
Technical write-up on how they setup this: https://annas-blog.org/how-to-run-a-shadow-library.html
Let’s start with our tech stack. It is deliberately boring. We use Flask, MariaDB, and ElasticSearch. That is literally it. Search is largely a solved problem, and we don’t intend to reinvent it.
Source: @sebsauvage