
Stirling-PDF is a robust, locally hosted web-based PDF manipulation tool using Docker. It enables you to carry out various operations on PDF files, including splitting, merging, converting, reorganizing, adding images, rotating, compressing, and more. This locally hosted web application has evolved to encompass a comprehensive set of features, addressing all your PDF requirements.

Project documentation: pdfly.readthedocs.io
pdfly is the youngest project of the py-pdf organization.
It has been created by Martin Thoma in 2022.
It's simply a CLI tool to manipulate PDF files, written in Python and based on the fpdf2 & pypdf libraries.
I'm a maintainer of the project 🙂
What can it do & what's next?
Find out by reading the full article
Outil permettant la mise à l'échelle de n'importe quelle image de style "anime", par le biais de réseaux de neurones convolutionnels. Fonctionne également sur les photos.
Open-source: https://github.com/nagadomi/nunif
⚡ Fast, async, stream-based link checker written in Rust. Finds broken URLs and mail addresses inside Markdown, HTML, reStructuredText, websites and more!
... and how to use them in CI pipelines.
Comparing W3C v.Nu HTML checke, html-tidy, htmlhint, html-validate, LintHTML and html-eslint.
Excellent self-hosted website monitoring tool written in Go.
I was able to set it up in less than an hour so that it triggers alerts to a webhook 👍
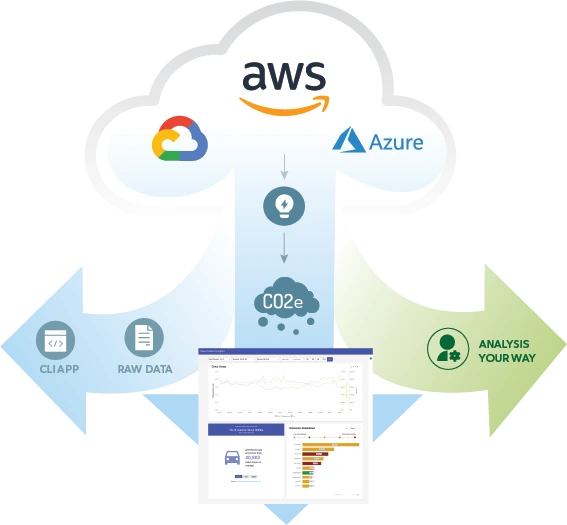
Cloud Carbon Emissions Measurement and Analysis Tool
Understand how your cloud usage impacts our environment and what you can do about it
Au cours des 18 derniers mois, j'ai eu l'occasion de concevoir plusieurs sites web pour des proches et des associations où je suis bénévole.
Dans cet article, je reviens sur mes choix de solutions pour les mettre en place, et partage mes réflexions concernant les alternatives pour concevoir de "petits …
A short Python script based on pypdf that checks if PDF files contain JavaScript code, and if applicable print it.

A mathematical puzzle game.
Découvrez les règles du jeu par vous-même en résolvant des problèmes simples. Vous découvrirez de nouvelles idées mathématiques !

A custom made variant of the Free-Cell solitaire, mostly inspired by the Shenzen Solitaire by Zachtronics, with pirate themed cards in pixel art.
Playable on android, I downloaded it with F-Droid.
I wrote my last post on fpdf2 18 months ago.
We released 7 more versions of fpdf2 since then!
This article will present some of the major features introduced since v2.7.3 to v2.8.1 of fpdf2:
click on the buttons below to reveal the various changes brought …
European Alternatives is a project that collects and analyzes European alternatives to digital services and products, such as cloud services and SaaS products. We regularly receive advice and suggestions from European Alternatives users, so feel free to reach out!
- Web analytics services
- Cloud computing platforms
- Content delivery network (CDN) services
- Email providers
- Virtual private server (VPS) hosters
- Search engines
- Transactional email service
- Domain name registrars
- Time tracking apps
- Navigation apps
- Uptime monitoring services
- File hosting services
- Machine translation services
- Object storage providers
- Microblogging services
- VPN services
- Managed DNS providers
- Professional networking platforms
- Function as a service (FaaS) providers
- Platform as a service (PaaS) providers
- Error tracking services
- Electronic signature software
- Public DNS resolvers
- Payment service providers
- Captcha services
- Spelling and grammar checkers
- Password managers
- Instant messaging apps
- Version control services
- Identity and access management (IAM) services
- Live chat software
- Web browsers
- Video conferencing software
- Document collaboration services
- Calendar services
- Email marketing services
- Font services
- WordPress hosting providers
- Team communication services
- Managed Kubernetes services
- Video hosting services
- Video platforms
- Maps API services
- Tag management systems
- DDoS protection services
- Session recording tools
- ACME SSL certificate providers
- Survey tools
- Marketing automation software
- Project Management Software
- SMS APIs
An open-source guide to help you write better command-line programs, taking traditional UNIX principles and updating them for the modern day.

Gauguin is a Sudoku-like game where you solve grids via calculation and logic.
Over a period of over two years, an attacker using the name “Jia Tan” worked as a diligent, effective contributor to the xz compression library, eventually being granted commit access and maintainership. Using that access, they installed a very subtle, carefully hidden backdoor into liblzma, a part of xz that also happens to be a dependency of OpenSSH sshd on Debian, Ubuntu, and Fedora, and other systemd-based Linux systems that patched sshd to link libsystemd.
That backdoor watches for the attacker sending hidden commands at the start of an SSH session, giving the attacker the ability to run an arbitrary command on the target system without logging in: unauthenticated, targeted remote code execution.The attack was publicly disclosed on March 29, 2024 and appears to be the first serious known supply chain attack on widely used open source software. It marks a watershed moment in open source supply chain security, for better or worse.
This post is a detailed timeline that I have constructed of the social engineering aspect of the attack, which appears to date back to late 2021.
A breakdown of what constitutes the software supply chain and how to secure each stage
Software Supply-Chain (SCC) attacks has become so critical that it has been driven by the government. The Biden Administration, in its second year in office, released an executive order on SSC risks. This has created a tailwind that has led to a proliferation of companies aiming to protect the supply chain and enable companies to comply with this legislation.
Bundling software components and dependencies into a deployable format and distributing it for installation on target systems. We discuss Software Bill of Materials (SBOM), code provenance and signatures, and artifact repositories.
tomato is a python script to glitch AVI files
It was designed to operate video frame ordering, substraction and duplication.