A breakdown of what constitutes the software supply chain and how to secure each stage
Software Supply-Chain (SCC) attacks has become so critical that it has been driven by the government. The Biden Administration, in its second year in office, released an executive order on SSC risks. This has created a tailwind that has led to a proliferation of companies aiming to protect the supply chain and enable companies to comply with this legislation.
Bundling software components and dependencies into a deployable format and distributing it for installation on target systems. We discuss Software Bill of Materials (SBOM), code provenance and signatures, and artifact repositories.
TL;DR: There are three options to fix an NPM dependency:
- Open a bug ticket on the repository of the maintainer
- Fork & Fix
- Create a patch and fix it
J'avais tendance à privilégier la 2e solution, mais elle a l’inconvénient de créer une dépendance à github.com au moment du build, ce qui n'est pas toujours pratique dans un contexte d'entreprise... patch-package peut donc s'avérer bien pratique dans ce cas
:format(webp)/cdn.vox-cdn.com/uploads/chorus_image/image/70367267/acastro_180109_1777_0001_v1.0.jpg)
$ npm install faker@6.6.6
LIBERTY LIBERTY LIBERTYArticle complémentaire FR: https://www.01net.com/actualites/au-bout-du-rouleau-un-developpeur-sabote-ses-logiciels-open-source-2053434.html

À oui.sncf, je travaille au sein d'une équipe en charge de l'usine logicielle,
qui administre depuis des années une instance Gitlab self-hosted.
Cet article contient quelques-unes de nos recommandations à l'intention des utilisateurs de notre Gitlab, ayant pour but à la fois améliorer les performances de leurs pipelines …
Effectively find upstream & downstream dependencies of a Pypi package
More about it: https://blog.acolyer.org/2020/09/21/watchman/
Alt: https://github.com/DavHau/pypi-deps-db
libraries.io also provides this information, possibly less accurate
Almost a year ago, GitHub introduced security alerts. They are an awesome feature.
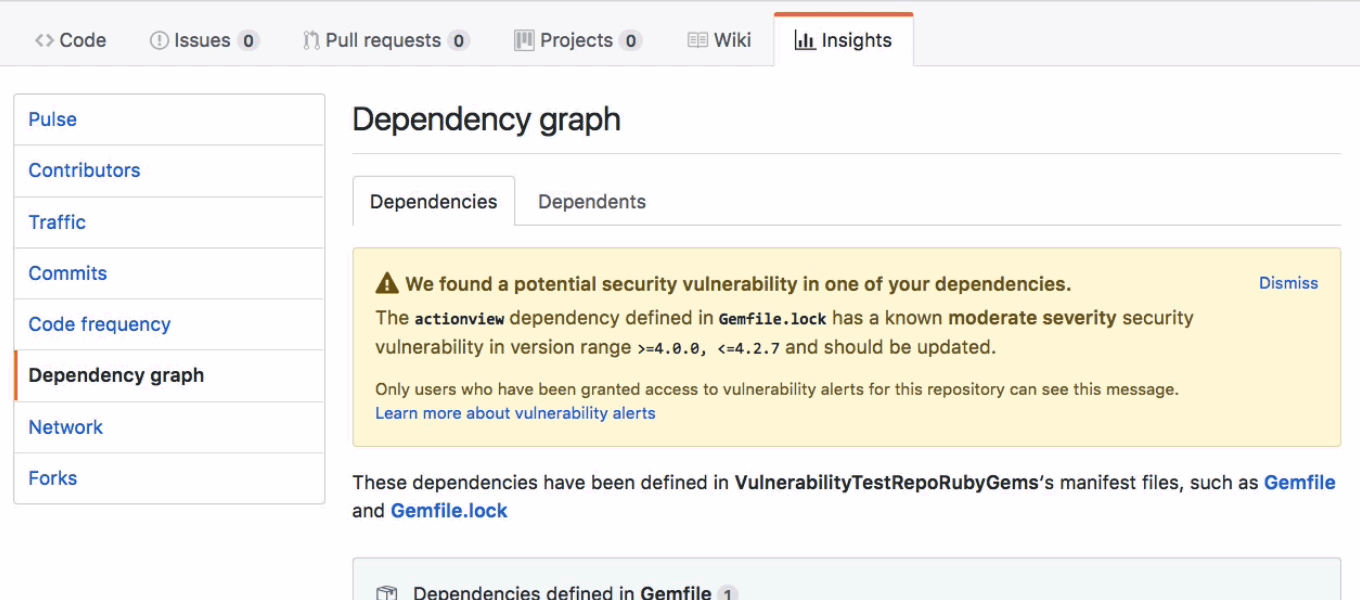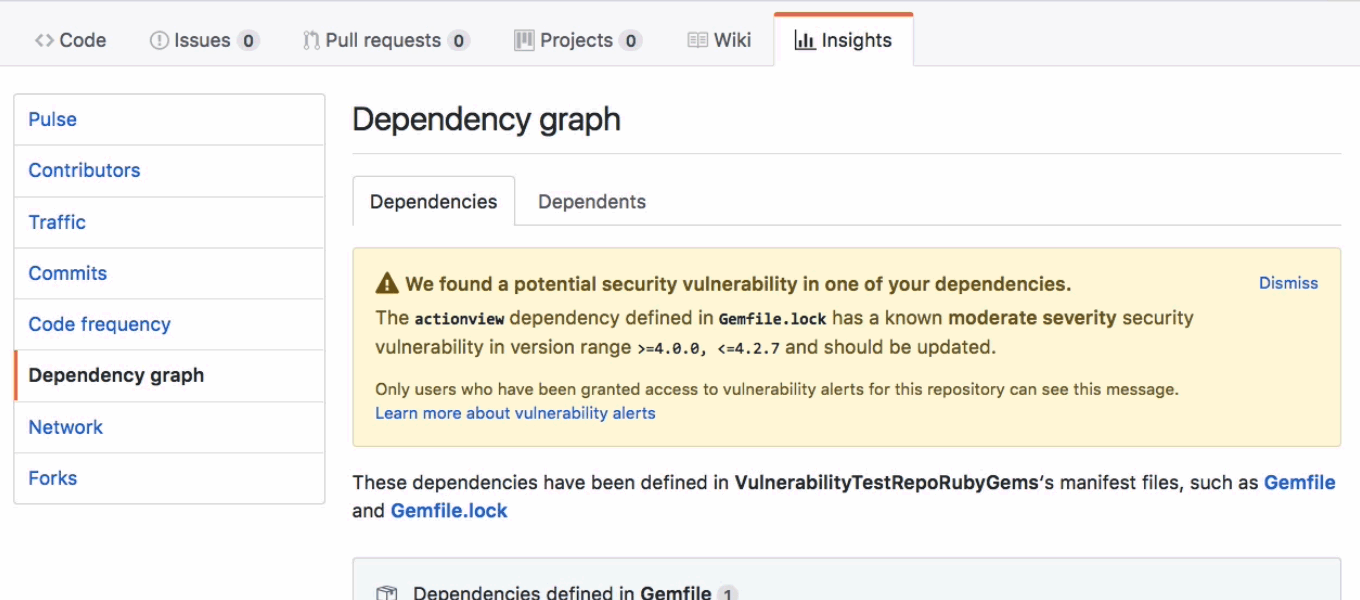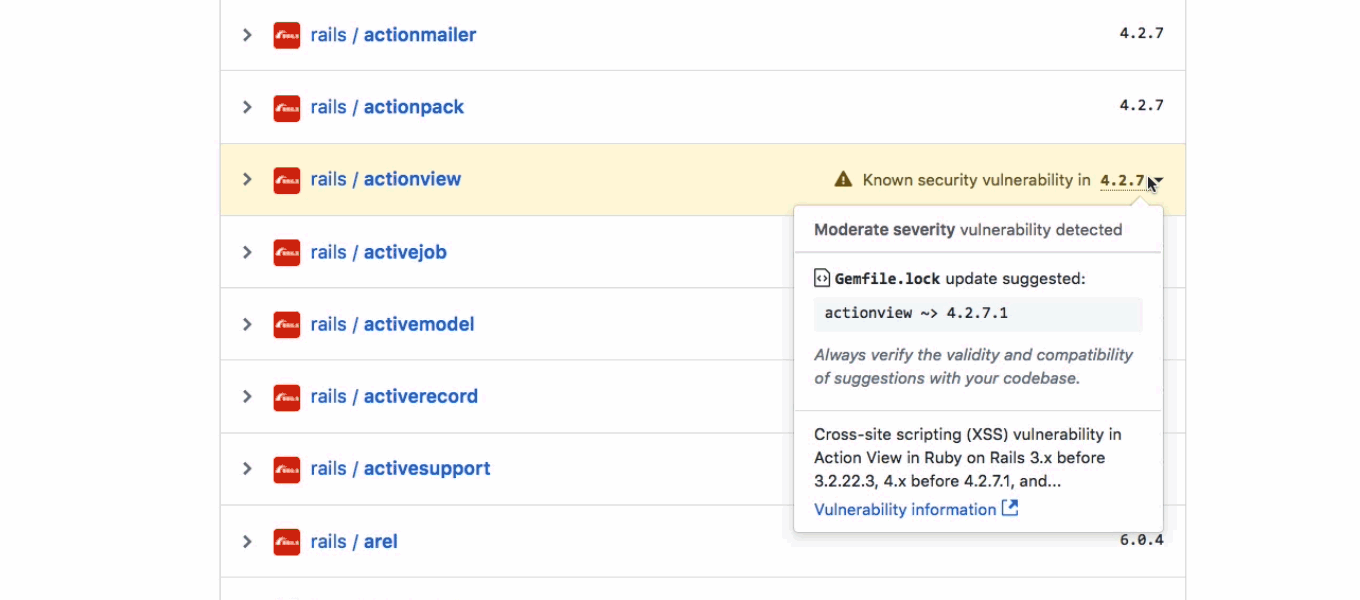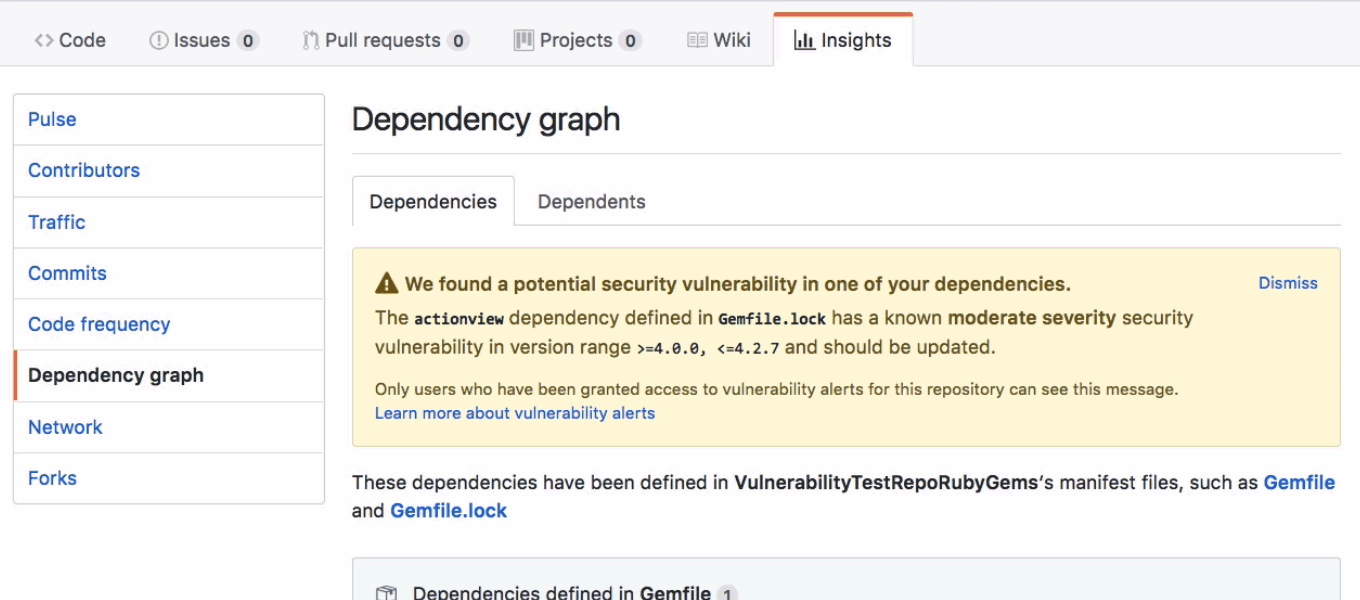
They function as notifications you receive whenever a vulnerability affecting one of your project dependencies.
But long after receiving a notification, how to list all security alerts affecting your repositories ?
I didn't found an out-of-the box solution …
I ended up not using this code, but it may be useful to others:
mock_setup_provider.py:
import sys
from unittest.mock import Mock
class MockSetupProvider(Mock):
def __init__(self, *args, **kwargs):
super().__init__(*args, **kwargs)
self.captured_setup_requires = set()
def setup(self, *args, **kwargs):
self.captured_setup_requires.update(kwargs.get('setup_requires'))
setup_extractor …