Je recommande cet épisode en particulier, avec un excellent REX / PostMortem de Stéphane Lenco sur une gestion de crise à Thalès, ciblé par le rançongiciel / ransomware LockBit
Another set articles covers the code in more depths:
- https://cybergeeks.tech/a-technical-analysis-of-pegasus-for-android-part-1/
- https://cybergeeks.tech/a-technical-analysis-of-pegasus-for-android-part-2/
- https://cybergeeks.tech/a-technical-analysis-of-pegasus-for-android-part-3/
Source: @ebsauvage
You can use this program but I wrote a simple python script which enumerates the exported functions from the provided DLL (
dll-def.py)A simple way to prevent DLL hijacking from happening would be for applications to always use absolute paths instead of relative ones. Although some applications (notably portable ones) will not always be able to do so, applications located in \system32\ and relying on DLLs in the same folder have no excuse for doing otherwise. The better option, which only very few Windows executables seem to do, is to verify all DLLs before loading them (e.g. by checking their signatures) - this would largely eliminate the problem.
Dans cet article, nous allons voir comment craquer une archive chiffrée protégée par un mot de passe en utilisant :
- L’attaque à clair connu de Biham et Kocher sur des archives Zip (PKZIP) basées sur la méthode de chiffrement ZipCrypto Store (peut être étendu à ZipCrypto Deflate).
- Une attaque classique par liste de mots sur d’autres archives chiffrées telle que les archives Zip (WinZip) basées sur la méthode de chiffrement AES (128,192,256), 7-Zip ou encore RAR.
Pour réaliser cette attaque, il faut au moins 12 octets de texte en clair connu et au moins 8 d’entre eux doivent être contigus. Plus le texte connu contigu est grand, plus l’attaque est rapide.
git-remote-gcrypt is a git remote helper to push and pull from repositories encrypted with GnuPG, using a custom format
Supported backends are local, rsync:// and sftp://, where the repository is stored as a set of files, or instead anywhere gcrypt will store the same representation in a git repository
The aim is to provide confidential, authenticated git storage and collaboration using typical untrusted file hosts or services.
Tested: it works fine and is very easy to setup:
git remote add gitcrypt gcrypt::git@...
git config user.signingkey ...
git config gcrypt.participants ...
git push gitcrypt masterTo encrypt only SOME files in a git repo, better look at git-crypt
L’Assurance maladie est victime d’un nouveau piratage de masse. Selon une enquête de ZATAZ, plus d’un million de Français voient désormais leurs données personnelles en vente sur le web pour la modique somme de 6000 dollars. Selon les experts en cybersécurité, il est probable que le hacker ait obtenu leurs identifiants grâce à une campagne de phishing.
un pirate mettrait actuellement en vente une immense base de données contenant 1 million d’identifiants et de mots de passe pour la plateforme Ameli
FROM sebsauvage
TL;DR version of lessons from the post:
- Writing open source software can be very rewarding in ways you can’t predict
- Be in it for the long haul
- Ship it and ship regularly
- Have broad, open-ended goals
- If you care enough, you’ll find the time
- No one cares about your unit test coverage
- There’s no shame in marketing
- Clear it with your employer
- Foster community
- Keep it enjoyable
Source: https://www.reddit.com/r/Python/comments/smta85/lessons_learned_from_my_10_year_open_source/
This person should be funded in a level that is appropriate for how critical log4j2 is used in the ecosystem. There is no excuse for this. This person's spare time passion project is responsible for half of the internet working the way it should.
TL;DR: If you want me to make you useful software, pay me. If you use software made by others in their spare time and find it useful, pay them. This should not be a controversial opinion. This should not be a new thing. This should already be the state of the world and it is amazingly horrible for us to have the people that make the things that make our software work at all starve and beg for donations.
adversaries can attack the encoding of source code files to inject vulnerabilities
The trick is to use Unicode control characters to reorder tokens in source code at the encoding level.
cf. https://fr.wikipedia.org/wiki/Fichier_de_test_Eicar
X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*FROM: https://sebsauvage.net/links/?0rGdAQ
Pour vous amuser à en créer en Python, avec fpdf2:
#!/usr/bin/env python3
# REQUIRE: pip install fpdf2 pdf417 qrcode
import fpdf, pdf417, qrcode
EICAR = 'X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*'
pdf = fpdf.FPDF()
pdf.add_page()
pdf.set_font("Helvetica", size=30)
pdf.text(90, 20, "EICAR")
pdf.text(10, 60, "PDF-417:")
pdf.image(pdf417.render_image(pdf417.encode(EICAR)), x=10, y=60)
pdf.text(10, 140, "QRCode:")
pdf.image(qrcode.make(EICAR).get_image(), x=35, y=145)
pdf.output("eicar.pdf")
À oui.sncf, je travaille au sein d'une équipe en charge de l'usine logicielle,
qui administre depuis des années une instance Gitlab self-hosted.
Cet article contient quelques-unes de nos recommandations à l'intention des utilisateurs de notre Gitlab, ayant pour but à la fois améliorer les performances de leurs pipelines …
il est facile, en utilisant de multiples sites web, de deviner des numéros de carte bancaire valides, et de deviner également les dates d'expiration et le CVV (cryptogramme visuel).
Visiblement, le système VISA est sensible à ce genre d'attaque, mais pas MasterCard.
Le principe consiste à entrer le numéro de carte sur de multiples sites web, et d'essayer de commander
Source : https://sebsauvage.net/links/

What happens if malicious code is uploaded to npm under these names? Is it possible that some of PayPal’s internal projects will start defaulting to the new public packages instead of the private ones?
tl;dr: User countermeasures:
- Noreply-Email-Address: Every GitHub user should either use a dedicated commit email address or GitHub’s noreply-email-address service, also enabling the option to block accidental command line pushes.
- 2-Factor-Authentication: Every GitHub user should have 2-Factor-Authentication enabled
- Raise Awareness: it’s the duty of developers aware of this issue toinform their colleagues about it
sed -i "s/$real_email/$github_email/" /opt/*/.git/config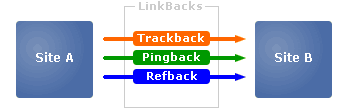
Linkback protocols are an old breed. They were born in a time where MySpace, Wikipedia & WordPress had just been born, and Friendster was more popular than this new website called Facebook.
The latest linkback protocol, Webmention, is relatively recent though, as it became a W3C …
Usine hydro-électrique, génératrice diesel, système d’aération, métro, silo, haut fourneau, système de production de bio-gaz ou d’eau potable… Tout y passe. Autant, les VNC d’avant, ça ne pouvait pas trop faire de dégat sinon la compromission de la machine en question, autant là on parle de systèmes qui peuvent conduire à des morts…
Issue #5 is out !

Paged Out! is a new experimental (one article == one page) free magazine about programming (especially programming tricks!), hacking, security hacking, retro computers, modern computers, electronics, demoscene, and other similar topics.
Issue #2 includes a crazy prime Python quine ! (page 35) O.O
This article shows how to construct a non-recursive zip bomb that achieves a high compression ratio by overlapping files inside the zip container. "Non-recursive" means that it does not rely on a decompressor's recursively unpacking zip files nested within zip files: it expands fully after a single round of decompression. The output size increases quadratically in the input size, reaching a compression ratio of over 28 million (10 MB → 281 TB) at the limits of the zip format. Even greater expansion is possible using 64-bit extensions. The construction uses only the most common compression algorithm, DEFLATE, and is compatible with most zip parsers.
$ python3 -m zipfile -e overlap.zip .
Traceback (most recent call last):
...
__main__.BadZipFile: File name in directory 'B' and header b'A' differ.How does a tiny repo cause git to run out of memory? The secret is that git de-duplicates “blobs” (which are used to store files) to make repositories smaller and allow using the same blob when a file remains unchanged between commits. Git also allows de-duplication of “tree” objects (which define the directory structure in a repository).
git-bombtries to make a billion files, however it only has 10 references to the file blob and only has 10 tree objects in all.
Almost a year ago, GitHub introduced security alerts. They are an awesome feature.
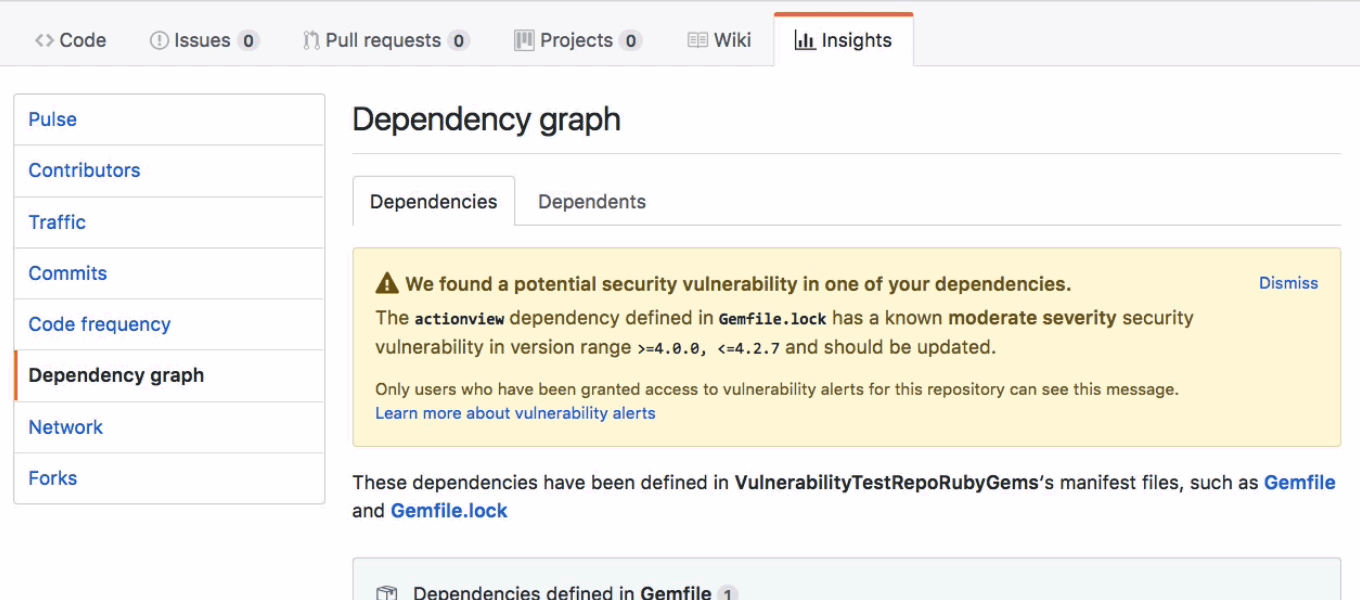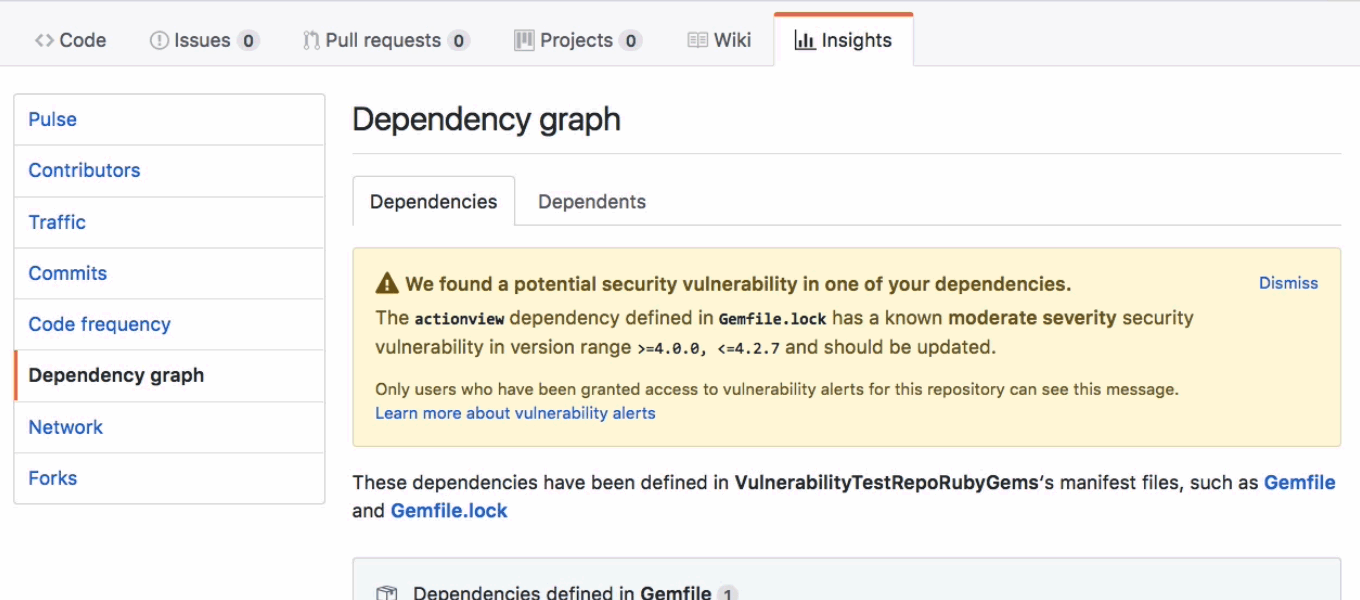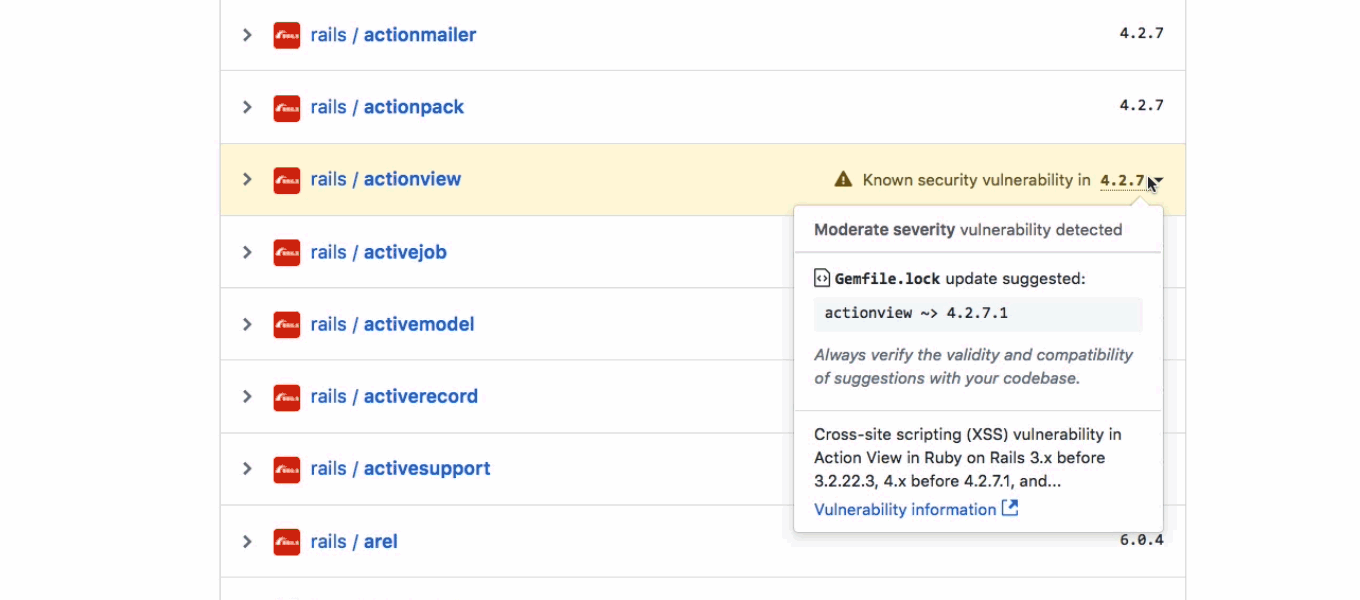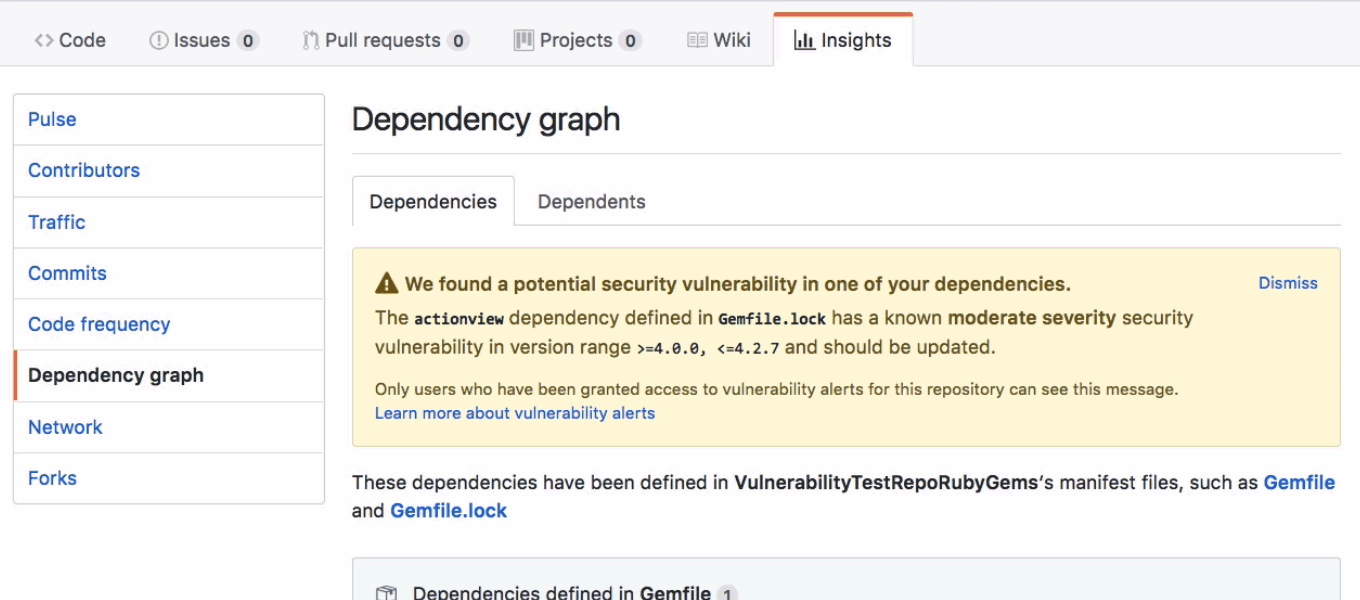
They function as notifications you receive whenever a vulnerability affecting one of your project dependencies.
But long after receiving a notification, how to list all security alerts affecting your repositories ?
I didn't found an out-of-the box solution …